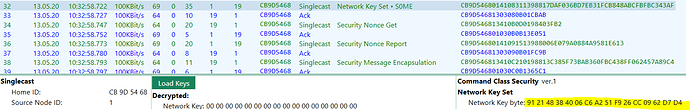
Hi!
I’m troubleshooting devices on my VeraPlus-network using the SiLab’s Z-Wave sniffer “Zniffer” (model ACC-UZB3-S). The tool supports decoding encrypted packets if the correct encryption key is provided. Are there any official/unofficial ways of extracting them from the VeraPlus?
I looked at the following tools on the VeraPlus:
/usr/bin/nvram
/usr/bin/zwave_uart_prog
/usr/bin/zwaveserial
…but didn’t find quite what I was looking for. Are there any Z-wave serial API commands which enables retrieval of the key, or should I attempt to parse the Z-wave network backup file?