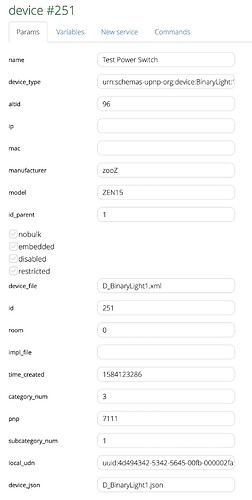
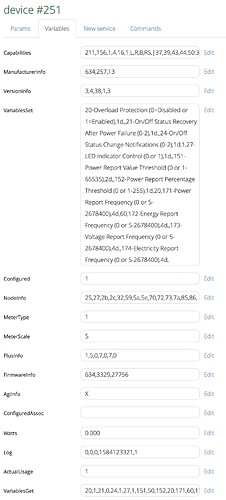
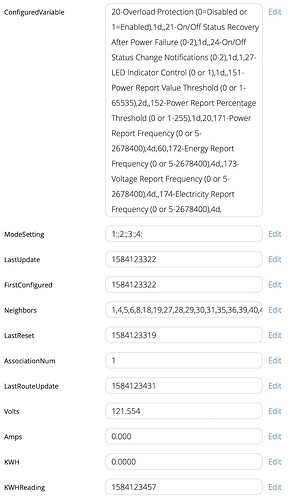
@Ioana, just a followup on running the spread daemon under a non-root user and the unprotected 4803 socket.
- As a quick test, I added a spread user and group to
/etc/passwd and /etc/group respectively and added DaemonUser = spread and DaemonGroup = spread to /etc/spread.config. I changed the owner of /var/firmware/log/spread.log to spread. For reference, here are the specific changes that I made:
/etc/passwd
root:x:0:0:root:/root:/bin/ash
daemon:*:1:1:daemon:/var:/bin/false
ftp:*:55:55:ftp:/home/ftp:/bin/false
network:*:101:101:network:/var:/bin/false
nobody:*:65534:65534:nobody:/var:/bin/false
spread:*:1111:1111:spread:/var:/bin/false
/etc/group
root:x:0:
daemon:x:1:
adm:x:4:
mail:x:8:
audio:x:29:
www-data:x:33:
ftp:x:55:
users:x:100:
network:x:101:
nogroup:x:65534:
spread:x:1111:
/etc/spread.conf
DaemonUser = spread
DaemonGroup = spread
>>AFTER RESTART<<
Conf_load_conf_file: using file: /etc/spread.conf
Successfully configured Segment 0 [127.0.0.255:4803] with 1 procs:
localhost: 127.0.0.1
ENABLING Dangerous Monitor Commands! Make sure Spread network is secured
Set runtime directory to '/var/run/spread'
Set runtime directory to '/var/run/spread'
Set user name to 'spread'
Set group name to 'spread'
Finished configuration file.
Hash value for this configuration is: 3871598377
Conf_load_conf_file: My name: localhost, id: 127.0.0.1, port: 4803
Spread: SECURITY RISK! running as root, but unix domain socket is not in a root-only writable directory. May risk denial of service or malicious deletion of unexpected file in directory: /tmp
ps w | grep spread | grep -v spread
6786 spread 2888 S /usr/sbin/spread -c /etc/spread.conf
Voila! Spread is no longer running as root.
-
BUT!!! The
SECURITY RISK message is back!!
I downloaded the spread toolkit source code and reviewed the configure options for a potential root cause for the spread sockets being opened in /tmp regardless of the RuntimeDir setting. I believe that the firmware build system sets the spread configure option --with-unix-socket-dir=/tmp which isn’t the best. It would be better to set it to /var/run/spread
root@8775fe673d9d:/tmp/spread-src-4.4.1# ./configure --help=short
Configuration of Spread 4.4.0:
Optional Packages:
--with-PACKAGE[=ARG] use PACKAGE [ARG=yes]
--without-PACKAGE do not use PACKAGE (same as --with-PACKAGE=no)
--with-cflags Specify additional flags to pass to compiler
--with-cppflags Specify additional flags to pass to preprocessor
--with-ldflags Specify additional flags to pass to linker
--with-libs Specify additional libraries to link with
--with-mantype=man|cat|doc Set man page type
--with-pid-dir=PATH Specify location of spread.pid file
--with-unix-socket-dir=PATH Specify location of Unix Domain Socket for client-daemon connections. If you are running Spread as a root user, you should define this to be a root only directory such as /var/run to avoid some security risks.
Finally, the team probably wants to update spread to version 4.1.4 vs. the current Linux firmware version 4.0.4 from May 2014.
Spread Security Recommendations:
- Configure
spread build options to use /var/run/spread as the backing store for spread sockets
- Run
spread under spread user and group (i.e. non-root). This entails adding a spread user and group id, modifying /etc/spread.conf to use them, and adjusting any permissions set by scripts like /opt/bin/firmware/spread.sh and /etc/init.d/spread to the spread user.
- Optional: upgrade
spread 4.0.4 to 4.1.4
Doing these two pretty trivial development tasks should address the spread security issues. I realize this is alpha software but security is paramount for any device connected to the Internet and sometimes is more difficult to fix security issues later in the release cycle.
![]()
![]()